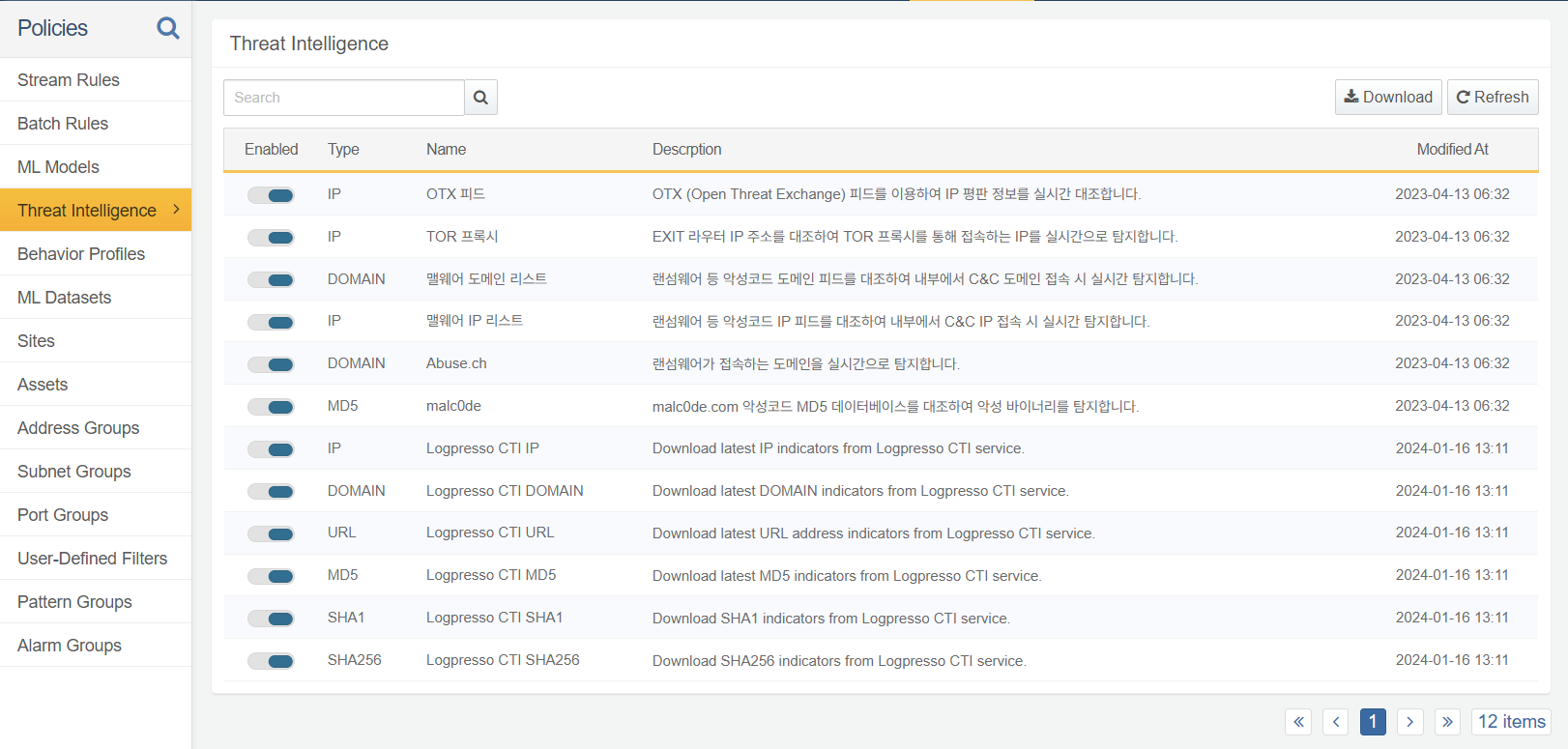
Threat Intelligence Feeds
You can manage the threat intelligence feeds provided by Logpresso CTI and Watchade ISAC under Policies /> Threat Intelligence. To receive specific feeds, activate each feed item. Only cluster administrator can activate/deactivate threat intelligence feeds, while administrators or users can only view the threat intelligence feed list.
The scenario builder of Stream Rule, the matchfeed query command, and the matchfeed() function match specific IP addresses, domain addresses, URLs, MD5 hashes, SHA1 hashes, or sHA256 hashes against the threat intelligence feeds to detect threats.
To use Logpresso CTI feeds, create a Logpresso CTI connect profile from the Connect Profiles. Customers with a paid Logpresso CTI subscription will receive real-time information; while free subscribers receive threat intelligence information with a 90-day delay.